Sws101_owasp
Topic: OWASP Top 10 -2021
Overview
Learning and exploiting each of the OWASP(Open Web Application Security Project) Top 10 vulnerabilities; the 10 most critical web security risks.The list is chosen by experts in web security through community feedback, incident analysis, trend tracking, and prioritization of vulnerabilities.
1. Broken Access Control
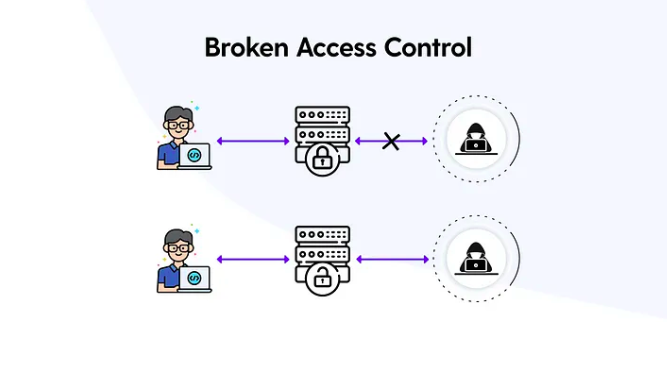
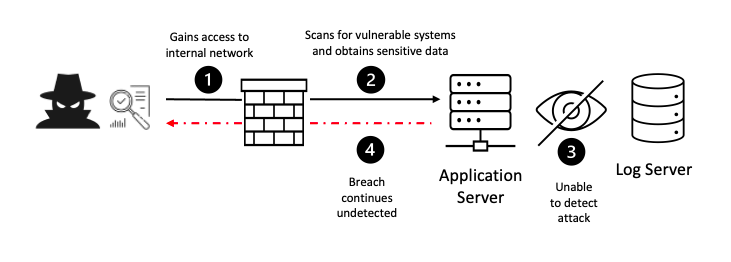
OWASP lists broken access control as the #1 critical web application security risk. Broken access control vulnerability is a security flaw that allows unauthorized users to access, modify, or delete data they shouldn’t have access to and it occurs when an application fails to properly enforce access controls, allowing attackers to bypass authorization and perform tasks as if they were a legitimate user. It rose from the top 5 in the OWASP Top 10-2017 list to the number 1 position in 2021.
This vulnerability can exist in various forms, and one of them is insecure direct object references (IDOR). Insecure Direct Object Reference (IDOR) is a vulnerability that arises when attackers can access or modify objects by manipulating identifiers used in a web application’s URLs or parameters.
For example, consider an application that uses database keys in its URLs. An attacker could change the key in the URL to access another object, which might contain sensitive data. If the application doesn’t verify the user’s access rights before serving the requested data, it’s vulnerable to an IDOR attack.
Ways to prevent broken access control:
Least Privilege: Give users only the access they need, nothing more. Regularly review and update access levels as roles change.
Secure Sessions and Authentication: Ensure each user has a unique session and use strong authentication methods like passwords and multi-factor authentication.
Regular Audits: Conduct regular checks to make sure access controls are working as intended and revoke unnecessary access rights.
Error Handling and Logging: Handle errors carefully to avoid revealing sensitive information, and keep logs of all user actions to detect suspicious behavior.
2. Cryptographic Failures
Cryptographic failures are where attackers often target sensitive data, such as passwords, credit card numbers, and personal information, when you do not properly protect them. It can lead to data breaches, loss of intellectual property, and financial loss.
Some common examples are:
- Sensitive data is transmitted (via HTTP, FTP, SMTP, etc) or stored in clear-text (database, files, etc).
- Use of old or weak cryptographic algorithms.
- Use of weak or default encryption keys or re-use of compromised keys.
Encryption in transit refers to encrypting data that is transferred between the client and server. Encryption at Rest refers to the encryption applied to the stored data.
Potential security risk of storing such databases underneath the root directory of a website is it could allow unauthorized access to sensitive data.
Ways to prevent cryptographic failures:
Choose Strong Methods: Use well-known and trusted encryption methods that are considered secure.
Handle Keys Securely: Keep encryption keys safe and change them regularly.
Implement Encryption Properly: Make sure encryption is correctly set up in your software and systems.
Use Secure Connections: When sending data over the internet, use secure protocols like HTTPS to encrypt it.
Encrypt Stored Data: Keep sensitive data encrypted when it’s stored on your computer or server.
Control Access: Only allow authorized users to access encrypted data.
Test for Security: Regularly check your systems for vulnerabilities and fix any issues.
Train Your Team: Teach your team about encryption best practices and how to use it securely.
Follow Standards: Adhere to industry standards and guidelines for encryption.
3. Injection
An injection flaw is a vulnerabilty which allows an attacker to insert malicious inputs into an application or relay malicious code through an application to another system.
Some common examples of injection include:
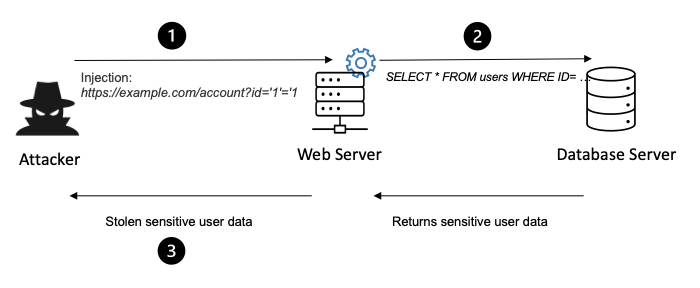
SQL injection: where malicious SQL (Structured Query Language) code is inserted into input fields of a web application, exploiting vulnerabilities in the application’s code to execute unauthorized SQL commands.Command injection: where attackers exploit vulnerabilities in software that dynamically constructs system commands, allowing them to execute arbitrary commands on the underlying operating system and this lets attackers control the server like they’re using it themselves.
Ways to prevent injection vulnerabilities:
Use Prepared Statements: Always use prepared statements with parameterized queries to treat user input as data, not part of the command.
Stored Procedures: Use stored procedures to separate data from commands, but ensure they are properly parameterized.
Input Validation: Validate user input against a list of acceptable values to prevent malicious data.
Escape User Input: Manually escape special characters in user input to prevent them from being interpreted as part of a command.
Safe APIs: Use APIs designed to prevent injection, which often provide a parameterized interface.
Restrict Database Code: Limit database functionality to prevent exploitation of vulnerabilities.
Keep Software Updated: Regularly update all application components to fix known vulnerabilities.
Monitor Inputs: Implement monitoring to detect and block injection attempts.
Configure Error Reporting: Avoid revealing sensitive information in error messages.
Avoid Shared Database Accounts: Use unique database accounts for different applications to limit the impact of compromised accounts.
Validate Input: Ensure input fields are validated for expected data types to accept only valid data.
4. Insecure Design
Insecure design vulnerabilities result from non-adherence to security best practices during the design process and it is one of the leading causes of functionality failures, data breaches, broken policies, and tarnished reputations. Insecure design vulnerabilities may also be introduced by developers while adding some “shortcuts” around the code to make their testing easier.
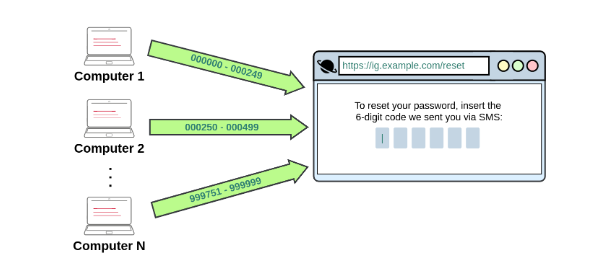
A good example of such vulnerabilities occurred on Instagram which allowed user to reset thier password by sending 6-digit code to thier mobile number via SMS for validation. Instagram had rate-limiting implemented so attackers attempted to bypass the rate-limiting system by utilizing numerous IP addresses to exploit this vulnerability and brute-force a 6-digit number. The problem of this vulnerabilites is in the design rather than the implementation of the application.
Ways to prevent insecure design:
Adopt a Secure Development Lifecycle (SDLC): Integrate security considerations from the start of the development process. This ensures that security is not an afterthought but is built into the application from the beginning .
Threat Modeling: Conduct detailed threat modeling for critical components like authentication, access control, and business logic. This helps identify potential threats early and design the system to mitigate these risks .
Use Secure Development Procedures: Implement secure development procedures that include secure coding practices and design patterns. This ensures that security is considered at every step of the development process .
Partner with AppSec Professionals: Collaborate with Application Security (AppSec) professionals to evaluate design security and privacy-related controls. Their expertise can help identify and address design flaws before they become vulnerabilities.
Implement Security Controls: Ensure the system has appropriate security controls in place, such as segregation at the system and secure communication layers, and limiting resource consumption by user or service. This helps protect against various types of attacks .
Move from DevOps to DevSecOps: Transition to a DevSecOps model, which integrates security practices into the development process. This ensures that security is considered alongside functionality and performance.
5. Security Misconfiguration
A security misconfiguration can occur when security settings are either not implemented, or deployed with errors.
Examples of Security misconfiguration :
Sample Applications Vulnerability: when you skip or miss removing sample applications that come packaged with the application server and you inject the same into the production server, you give hackers an opportunity since the sample applications contain known security gaps which can be exploited such as accessing the server through the default passwords.
Directory Listing Vulnerability: when you dont deactivate the directory listing on the server,attackers can access directories and download the compiled java classes and reverse engineer access to code and detect control flow in the application.
Error Message Vulnerability: when you set up a configuration that gives detailed error messages to the users which contains server’s important informations and flaws so the attackers will try to get the error message and get the information.
Default Privileges Vulnerability: cloud service provider have default sharing permissions which means confidential data such as privilege credentials are stored in the cloud.
Unnecessary Features Vulnerability: Unnecessary features are enabled or installed (e.g., unnecessary ports, services, pages, accounts, or privileges).
Improper Data Validation Vulnerability: Skipping proper data checks can invite cyberattacks, harming your app and organization.
Unpublished URLs Vulnerability: Keeping unused URLs active increases your app’s vulnerability. Shortening and blocking unnecessary URLs helps reduce the chance of attackers finding and exploiting them.
Out-of-date Software Vulnerability: the software is out of date or vulnerable
Ways to prevent Security Misconfiguration:
Adopt Repeatable Hardening Processes: A repeatable hardening process makes it fast and easy to deploy another environment that is appropriately locked down.
Automate Repetitive Tasks: An automated process to verify the effectiveness of the configurations and settings in all environments.
Regularly Update Software: A task to review and update the configurations appropriate to all security notes, updates, and patches as part of the patch management process.
Conduct Frequent Audits: Employ periodic inspection to detect and mitigate potential security misconfigurations and appsec risks.
Build Segmented Architecture: A segmented application architecture provides effective and secure separation between components or tenants, with segmentation, containerization, or cloud security groups (ACLs).
Avoid Unused Features: A minimal platform without any unnecessary features, components, documentation, and samples. Remove or do not install unused features and frameworks.
Debugging tools help developers find and fix problems. Sometimes,these tools are left active when the software is released, creating security risks. Attackers can exploit these tools to run unauthorized commands.
Example, Patreon was hacked in 2015 due to an open debug interface in Werkzeug, a component in Python-based web apps. Leaving debugging tools on in released software is a serious security issue.
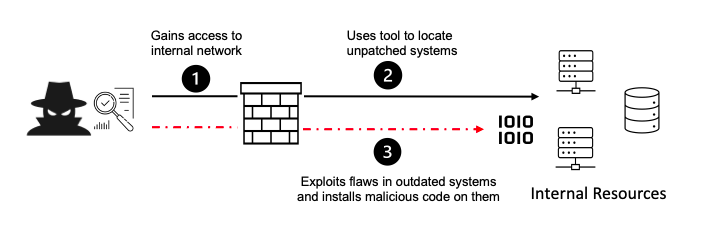
6. Vulnerable and Outdated Components
Vulnerable and outdated components refer to when open-source or proprietary code contains software vulnerabilities or is no longer maintained.
You are likely vulnerable:
If you do not know the versions of all components you use.
If the software is vulnerable, unsupported, or out of date. This includes the OS, web/application server, database management system (DBMS), applications, APIs and all components, runtime environments, and libraries.
If you do not scan for vulnerabilities regularly and subscribe to security bulletins related to the components you use.
If software developers do not test the compatibility of updated, upgraded, or patched libraries.
Ways to prevent Vulnerable and outdated components vulnerability:
Implement Patch Management Process: Remove unused features, components, and documentation to reduce the attack surface.
Regularly Inventory Components: Keep track of software versions, including both client-side and server-side components and their dependencies.
Monitor for Vulnerabilities:Continuously check Common Vulnerability and Exposures (CVE) and National Vulnerability Database (NVD) for known vulnerabilities in components.
Source Components Securely: Only obtain components from official sources via secure links.
Monitor Maintenance Status: Keep an eye on libraries and components for signs of being unmaintained or not providing security patches for older versions.
7. Identification and Authentication Failures
Identification and authentication failures are security vulnerabilities that can occur when a system or application fails to identify or authenticate a user correctly.
for example:
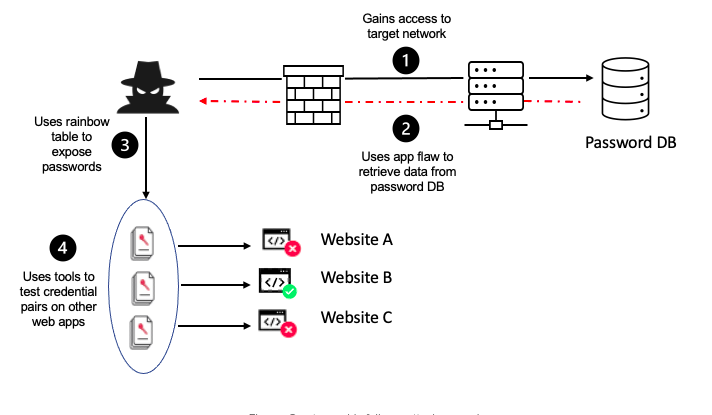
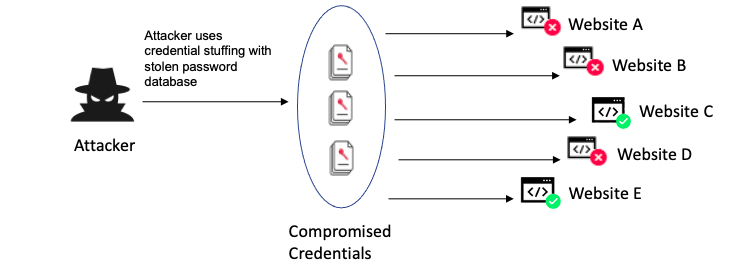
Brute Force Attack: An attacker repeatedly tries different combinations of usernames and passwords until they gain access, like trying “admin” with “password123”.
Weak Credentials: A user sets their password as “123456” or “password”, both easily guessable.
Weak Session Cookies:Session IDs are generated sequentially (session1, session2), allowing attackers to easily guess valid session IDs.
Multi-Factor Authentication (MFA): In addition to entering a password, users must also enter a one-time code sent to their mobile device.
Ways to prevent Identification and Authentication Failures:
Implement Multi-Factor Authentication (MFA): Require users to provide additional verification besides passwords, such as SMS codes, authenticator apps, or biometric data.
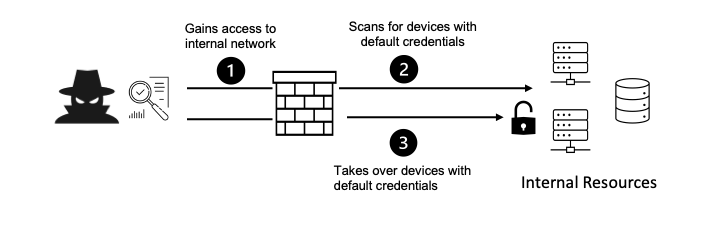
Avoid Default Credentials:Ensure that no default or easily guessable credentials, especially for administrative accounts, are shipped or deployed with the application.
Enforce Password Checks:Implement checks against common weak passwords to prevent users from setting easily guessable passwords.
Follow Password Guidelines: Align password policies with NIST 800-63b guidelines, focusing on factors like length, complexity, and rotation.
Harden Registration and Credential Recovery:Protect against account enumeration attacks by using consistent messaging for all outcomes during registration, credential recovery, and API pathways.
Limit Failed Login Attempts:Restrict or delay failed login attempts to mitigate brute force attacks, while monitoring and logging such attempts for alerting administrators.
Use Secure Session Management: Utilize a server-side, secure session manager that generates random session IDs with high entropy.
- Ensure session identifiers are not included in URLs, securely stored, and invalidated after logout, idle, or absolute timeouts.
8. Software and Data Integrity Failures
Software and data integrity failures occur when unauthorized changes or modifications are made to software or data, compromising their accuracy, reliability, and trustworthiness. These failures can lead to severe consequences, including data corruption, loss of trust, and security breaches.
Examples of Software and Data Integrity Failures:
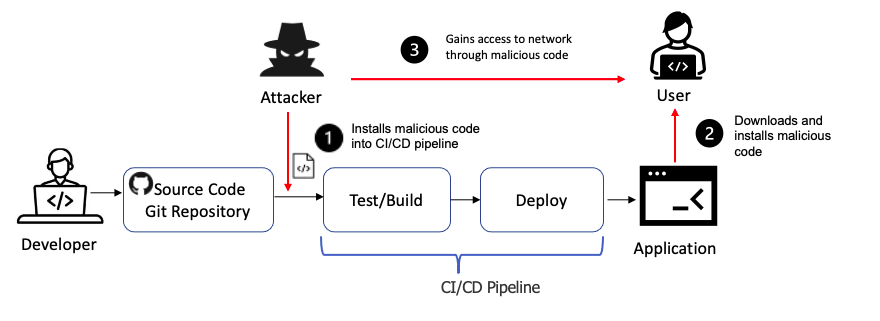
Unauthorized Modification of Software: Hackers exploit vulnerabilities to alter the code of software, introducing malicious code or backdoors.
Data Tampering: Attackers manipulate data stored in databases or files, altering its content to gain unauthorized access or disrupt operations.
Malware Infections: Malicious software infects systems, compromising the integrity of files, applications, and system configurations.
Insider Threats: Employees or insiders intentionally or unintentionally modify software or data, leading to integrity breaches.
Supply Chain Attacks: Attackers compromise software during its development or distribution process, injecting malicious code or components.
Ways to Prevent Software and Data Integrity Failures:
Implement Code Signing: Digitally sign software releases to verify their authenticity and detect unauthorized modifications.
Use Cryptographic Hashing: Hash functions can ensure the integrity of data by generating unique hash values for files and comparing them to detect changes.
Apply Access Controls: Restrict access to sensitive systems, files, and data to authorized personnel only, reducing the risk of unauthorized modifications.
Employ File Integrity Monitoring (FIM): Continuously monitor critical files and directories for unauthorized changes using FIM tools to detect and respond to integrity breaches.
Secure Development Practices: Follow secure coding practices, conduct code reviews, and perform security testing to identify and mitigate vulnerabilities in software.
Regular Software Updates: Keep software and systems up-to-date with security patches and updates to address known vulnerabilities and reduce the risk of exploitation.
Educate Employees: Train employees on security awareness and best practices to prevent insider threats and ensure they understand the importance of maintaining software and data integrity.
9. Security Logging and Monitoring Failures
Security logging and monitoring failures occur when inadequate or ineffective logging and monitoring mechanisms are in place, leading to difficulties in detecting and responding to security incidents and breaches.
Examples of Security Logging and Monitoring Failures:
Incomplete Logging: Insufficient logging of security events, such as failed login attempts, system changes, or unauthorized access, hinders incident detection and investigation.
Lack of Centralized Monitoring: Failure to aggregate and centrally monitor logs and security events from various sources makes it challenging to correlate and analyze them effectively.
Failure to Define Baselines: Without established baselines for normal system behavior, detecting anomalous activities indicative of security incidents becomes challenging.
Failure to Monitor Critical Systems: Inadequate monitoring of critical systems and assets increases the risk of undetected security breaches and compromises.
Lack of Alerting Mechanisms: Absence or misconfiguration of alerting mechanisms to notify security personnel of suspicious activities or potential security incidents results in delayed response times.
Ways to Prevent Security Logging and Monitoring Failures:
Establish Logging Policies: Define comprehensive logging policies specifying what events to log, retention periods, and log storage mechanisms to ensure consistent and effective logging.
Implement Centralized Logging: Aggregate logs from diverse sources into a centralized logging platform for efficient monitoring, analysis, and correlation of security events.
Define Alerting Thresholds: Set up alerting thresholds based on predefined criteria to promptly notify security teams of suspicious activities or deviations from normal behavior.
Conduct Regular Log Reviews: Perform regular reviews of logs and security events to identify anomalies, detect security incidents, and initiate timely incident response actions.
Invest in Security Information and Event Management (SIEM): Deploy SIEM solutions to automate log aggregation, analysis, and correlation, enabling proactive threat detection and response.
Train Security Personnel: Provide training to security personnel on effective log analysis techniques, incident response procedures, and utilization of monitoring tools to enhance security posture.
10. Server-Side Request Forgery (SSRF)
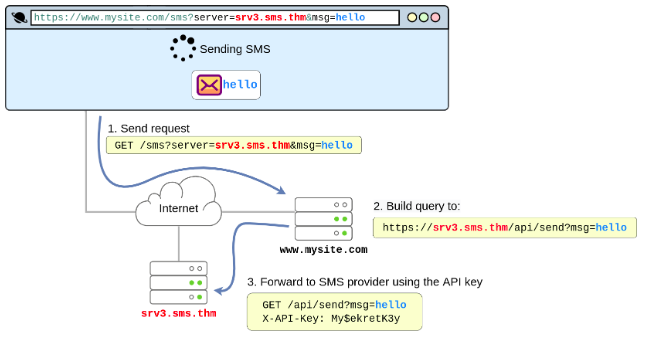
A Server-Side Request Forgery (SSRF) attack involves an attacker abusing server functionality to access or modify resources. The attacker targets an application that supports data imports from URLs or allows them to read data from URLs. URLs can be manipulated, either by replacing them with new ones or by tampering with URL path traversal.
Let’s see an example.
The vulnerability lies in the web application’s exposure of the “server” parameter, which specifies the SMS service provider’s server name. An attacker can manipulate this parameter to redirect requests to their own server. By crafting a request with their server address, the attacker can intercept the API key included in the request to the SMS provider. This allows the attacker to send messages using the SMS service at the expense of the web application owner. To exploit this, the attacker simply needs to change the server parameter in the URL to their own server address, enabling them to capture the API key and misuse the SMS service.
SSRF can be used for:
- Enumerate internal networks, including IP addresses and ports.
- Abuse trust relationships between servers and gain access to otherwise restricted services.
- Interact with some non-HTTP services to get remote code execution (RCE).
Ways to prevent SSRF:
Whitelisting: Only allow URLs/hosts that you know are safe.
Block Private IPs: Ensure the application logic blocks requests to private IP address spaces.
Minimal Permissions: Run services with minimal permissions to eliminate the SSRF vulnerability or so that, even if there’s an SSRF vulnerability, the damage can be contained.
Up-to-date Libraries: Ensure all libraries/frameworks are updated regularly. Some older libraries have known SSRF vulnerabilities.
Timeouts: Implement reasonable timeouts to prevent attackers from access sensitive resources, especially if those sensitive resources are associated with slower response times (e.g. from 1 query on 1 large chunk of sensitive data).